Advanced network capture configuration
Important
This article provides additional information on configuring network packet capture for experienced users.
The following features are available when working with the Network packet capture module:
With large volumes of network traffic passing through, some packets may be discarded because the router will not have time to process them. Therefore, it is recommended to use filters, specify capture directions, and limit third-party traffic during diagnostic collection.
The file is recorded cyclically. If the specified size is exceeded, the beginning of the recording is erased, and new information is gradually added to the end of the file.
Next, we will take a closer look at the packet capture settings.
Connection — the interface for which packet capture is performed. Usually, if there are problems with the router, it is necessary to collect traffic from an active Internet connection (this can be a WAN ISP interface or a connection through a USB modem). If a tunnelled connection (PPTP, L2TP, PPPoE) is used to connect to the ISP, traffic must be collected from this interface. In case of problems with traffic flow or port forwarding, it is recommended to collect traffic from both the WAN interface (e.g. ISP) and the Home network interface.
Storage location specifies the location for saving the file in Wireshark format (*.pcap extension) containing the captured packets. If an external USB drive is selected, an additional Storage folder field appears, where you must define the path to the folder on the external USB drive. If Internal storage is selected, the file will be saved to the router's internal memory. If an external USB drive with sufficient free memory (at least as much as the internal memory) is connected to the router, it is recommended to use it to ensure that more useful information can be stored.
Buffer size sets the size of the buffer for temporarily storing packets in the capture library (or kernel, depending on the platform). The minimum value is 64 KB, the maximum is [RAM size in KB]/16. For example, for the KN-1711 model, the maximum buffer size can be 128*1024/16 = 8192 KB. It is recommended to set the maximum possible value for a particular model in order to collect the most complete packet dump.
Maximum file size — the maximum size of the output file with captured packets. The size is specified in kilobytes. If this parameter is set, the capture is performed in a circular buffer and saved to the output file at the end of the capture session. This parameter is required for devices that do not have a USB storage. The minimum value is 64 KB, the maximum is [RAM size in KB]/16. For example, for the KN-1711 model, the maximum buffer size can be 128*1024/16 = 8192 KB.
Maximum packet size specifies the maximum amount of data that will be saved from the received frame. The parameter always returns the configured value. The default value is 1518, the acceptable range is [1...16380].
Traffic type to capture determines what type of traffic will be captured (incoming/outgoing/both). The default value is Incoming and outgoing. The selected setting is always saved in the configuration.
Capture filter specifies a string describing the packet filter in Berkeley packet filter format. The filter syntax is the same as that used in Wireshark.
Filter usage examples:
ip host x.x.x.x — a filter that captures only packets with the address x.x.x.x
tcp dst port 80 — a filter that captures only HTTP packets (destination port tcp 80)
ip proto \icmp — a filter that captures only ICMP requests (ping)
udp port 53 — a filter that captures requests and responses exchanged with a DNS server
udp port 67 or udp port 68 or arp — a filter that captures DHCP and ARP requests exchanged
Timeout sets the timeout value when reading a packet from the interface, in milliseconds. Always returns the configured value. The default value is 1000. The acceptable range is [10...10000].
Promiscuous mode — enables the logic to record all packets, including those not intended for the selected interface. In normal mode, such packets are discarded.
For example, let's consider capturing network packets from a PC on a home network to track ICMP requests between that PC and a resource on the Internet. In this case, packet capture should be performed from the Home segment interface and the external (WAN) interface of the router connected to the Internet (in our example, this is the ISP interface).
The IP address of the PC on the local network is 192.168.4.34, and the IP address on the ISP's WAN interface is 46.72.188.17
The Internet resource to which we send ping requests is 8.8.8.8 (in our example, this is Google's public DNS server).
Two filters must be created (for the Home segment and ISP interfaces):
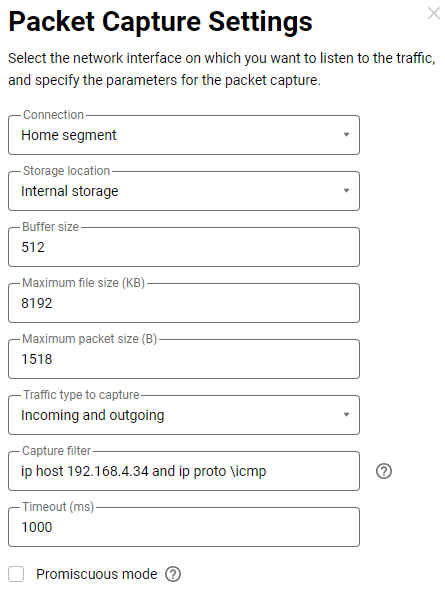
1. On the local network, you need to filter packets with the IP address 192.168.4.34 using the ICMP protocol.
The filter will be: ip host 192.168.4.34 and ip proto \icmp
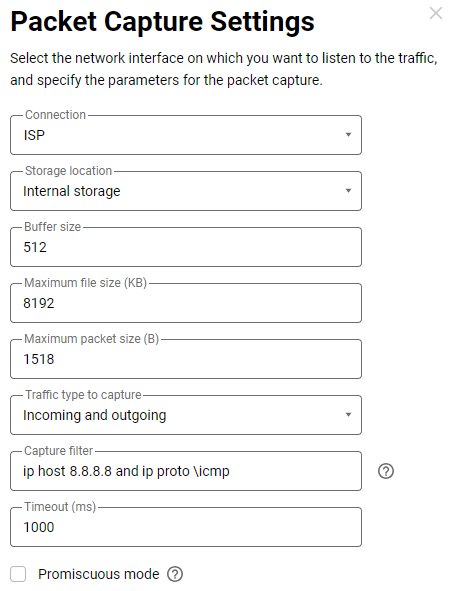
2. On the WAN interface, you need to filter packets by IP address 8.8.8.8, to which the local network PC sends ICMP requests, and by the ICMP protocol.
The filter will be: ip host 8.8.8.8 and ip proto \icmp
As a result, two rules will be created, which you need to enable by clicking the Start button.
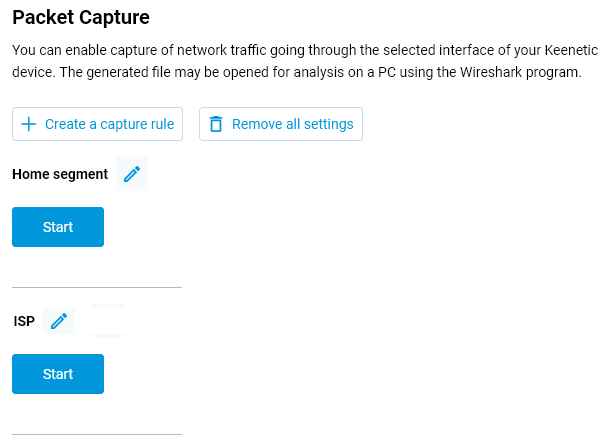
After starting network traffic capture, the router will begin collecting packets that match the specified filters. When the module is running, you need to ping the specified Internet resource from a computer on the local network:
ping 8.8.8.8 -t
After several ping attempts (successful or unsuccessful), stop packet capture by clicking the Stop button. To view the *.pcap file, use the Wireshark network traffic analyser.
Important
When contacting our technical support service, in addition to the network traffic dump file (*.pcap) obtained as a result of packet capture, you must provide the system file self-test.txt. Save it immediately after performing a packet capture. The information in a single *.pcap file without self-test.txt will be useless, as it is impossible to determine the conditions under which the packet capture was performed from the dumps alone.