The 'ip static' command for configuring NAT
How do I fine-tune NAT (Network Address Translation) in a router via the command-line interface (CLI) using the ip static command?
Important
This article is intended for experienced users.
It provides the syntax, detailed description, and examples of the ip static command for various NAT (Network Address Translation) settings. You need to work with this command through the device's command-line interface (CLI). After configuring the ip static command, you must execute the system configuration save command to save the settings to the router's non-volatile memory.
1. Description and usage of the 'ip static' command
This command allows you to create a static binding of local IP addresses to global ones. If interface or network corresponds to an interface with a public security level (the security-level public parameter is set in the interface settings in the CLI), destination address translation (DNAT) will be performed. If to-address corresponds to an interface with a public security level, source address translation (SNAT) will be performed.
The TCP/UDP port number is always considered the destination port.
If network equals a single address and that address is equal to to-address, this rule will prohibit translation of the specified address, which could be performed based on the specified ip nat rules.
Important
ip static rules have higher priority than ip nat rules.
2. Syntax of the 'ip static' command
ip static [ <protocol>] ( <interface› | ( <address> <mask>) ) ( <port> through <end-port> (<to-address> | <to-host> | <to-interface>) | <port> (<to-address> | <to-host> | <to-interface>) [<to-port>] | <to-address> | <to-host> | <to-interface>)
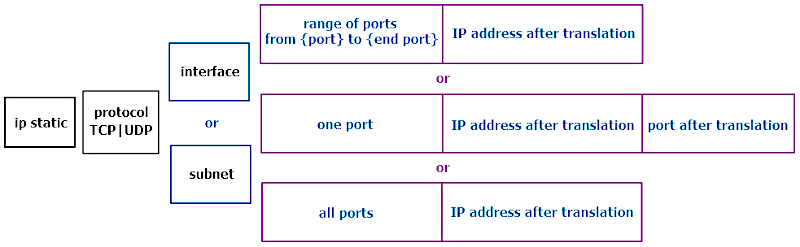
The rule can work either for one of two protocols (tcp or udp) or for all protocols (including icmp). If the tcp or udp protocol type is not specified, then it is not possible to select a port number in the syntax.
Let's look at the most commonly used examples of DNAT configuration with the ip static command.
Example 1. There is a server with the IP address 192.168.1.33 on the local network, to which access must be organised within the specified port range. After creating the rule, any request to the router's external IP address via TCP ports 10000 to 20000 will be redirected to the local server.
Forwarding the destination TCP port range from the external interface to the host on the local network:
ip static tcp ISP 10000 through 20000 192.168.1.33
This rule will forward TCP ports from 10000 to 20000 to the IP address 192.168.1.33.
Example 2. There is an IP camera with the address 192.168.1.33 on the local network, which needs to be accessed via UDP port 554 to view streaming video. In the video playback programme, you will need to open the address rtsp://WAN_IP:554.
Forwarding a single UDP destination port from the external interface to a host on the local network:
ip static udp ISP 554 192.168.1.33
This rule will forward UDP port 554 to the local IP address 192.168.1.33.
Example 3. There are several devices on the local network that have the same control port, and you need to configure remote access to each of them. It is impossible to open the same external port for different hosts at the same time, so you need to configure rules so that clients accessing different external ports are directed to the necessary device on the local network.
Translation of one external TCP destination port to another destination port on the local network:
ip static tcp ISP 8080 192.168.1.1 80
This rule forwards traffic to the external interface on port 8080 to traffic to the router on port 80.
Example 4. There is a server with IP address 192.168.1.33 on the local network, to which access must be provided on all ports.
Translation of requests on any external port to a host on the local network (DMZ, open server)
ip static ISP 192.168.1.33
3. Below are the most common examples of SNAT configuration using the 'ip static' command:
Example 1. The ISP provides two public IP addresses, and the Home subnet must be connected via one IP, while the Guest WiFi subnet must be connected via the other.
Connecting the router's local network via a global interface with a specific IP address:
ip static Home 180.100.100.10
This rule will apply to all packets coming from the local network (Home) to all global interfaces (the Use for accessing the Internet option is enabled in the interface settings), and the source IP address will be replaced with 180.100.100.10.
Important
This rule works independently of the ip nat Home rule, as ip static has the highest priority.
Example 2. The ISP provides two public IP addresses. There is a server on the local network, and it needs to be published on the Internet with its own IP address, while the rest of the network is published via the second IP address.
Bringing one host from the local network to the global network with a specific IP address (1-to-1 NAT):
ip static 192.168.1.33 255.255.255.255 180.100.100.10
This rule will only work for the local host 192.168.1.33, and it will exit through the global interface with the address 180.100.100.10. The rest of the local subnet will work according to the ip nat Home rule and will go to the global network with the source IP address registered on the external interface.
Important
For 1-to-1 NAT, you need to register an alias in the global interface settings using the following commands:
<config> interface ISP <config-if> ip alias 180.100.100.10 255.255.255.255
Example 3. There is a server with IP address 192.168.1.33 on the local network, which must access the external network with its own IP address for classic routing (without NAT).
Disabling the SNAT rule for a host on the local network:
ip static 192.168.1.33 255.255.255.255 192.168.1.33
This rule allows the local host with the address 192.168.1.33 and mask 255.255.255.255 to access global interfaces (WAN) with its local IP address. The rest of the local subnet will operate according to the ip nat Home rule and will connect to the global network with the source IP address registered on the external interface.
Notice
The ip static command can be used to enable NAT not only between an interface and an IP address, but also between two interfaces. For example:
ip static Home ISP
This will work when security-level public, is used on at least one of the interfaces for SNAT to work, as mentioned at the beginning of the article.
If interface or network corresponds to an interface with a public security level (the security-level publicparameter is set in the interface settings in the CLI), destination address translation (DNAT) will be performed. If to-address corresponds to an interface with a public security level, source address translation (SNAT) will be performed.